Me, looking at all the wonderful people engaging with my first post:
I want to thank everyone who supported me and read my last post and decided to come back! Onto the update.
This past week has been spent on modules 5-8, which consisted of Bash scripting, passive info gathering, active info gathering, and vulnerability scanning.
My wall of cheat sheets has grown quite a bit. Most of the topics are still a review, with a couple of exceptions for networking topics.
I don’t have any major hurdles to share this week. However, I want to discuss the incentives for the OSCP exam and how that relates back to study habits.
Learn the concept or the syntax?
In most of the Bash scripting exercises, the reader is instructed to solve the problem once in Bash, and once again in a higher level programming language (Python, Ruby, or php). I chose Python for every example because I have a decent amount of experience with it.
As I’ve programmed more and more over the years, I’ve always been told to learn the concept and not the language. I’ve come to appreciate this more and more. When duplicating an exercise in a higher level language, it ends up either clumsily put together to try and mimic Bash exactly, or I import a library that does almost all of the heavy lifting.
My first instinct is to always Google the problem and tack on “Python” to the end of the search. With these languages, someone has already solved the problem and it’s about reusing it and tweaking it to suit your needs. Most of the time I’d change the script to work better for my needs. For example, instead of hardcoding a target IP address, I’d change the script to accept it as a command line input. No major changes, just changing the I/O.
I’m learning a good amount of Bash, but going through the motions on Python. I understand why a higher level language is important - greater OS compatibility, more flexibility in uses, and good backup in cases where Bash is not acceptable. I remind myself that the goal is to have an alternative method ready even if it comes mostly through googling.
What does a practical exam incentivize?
From the OSCP website:
You have 23 hours and 45 minutes to complete the exam.
…
The exam consists of 3 independent targets and 1 Active Directory set (2 clients + 1 domain controller).
…
Your objective is to exploit each of the target machines and provide proof of exploitation. Each target machine contains at least one proof file (local.txt or proof.txt), which you must retrieve, submit in your control panel, and include in a screenshot with your documentation. Failure to provide the appropriate proof files in a screenshot for each machine will result in zero points being awarded for the target.
The expectations are clear and concise - compromise the machines and document it. There are some restrictions noted on not using professional/enterprise tools or Metasploit. The exam will test the knowledge I’ve gained and how well I can put it into practice.
An issue I envision is while studying, I do not learn about the “why” of exploitation as much as I learn the “how”. Learning how to compromise a system and properly document it is great and the OSCP is giving me that skillset.
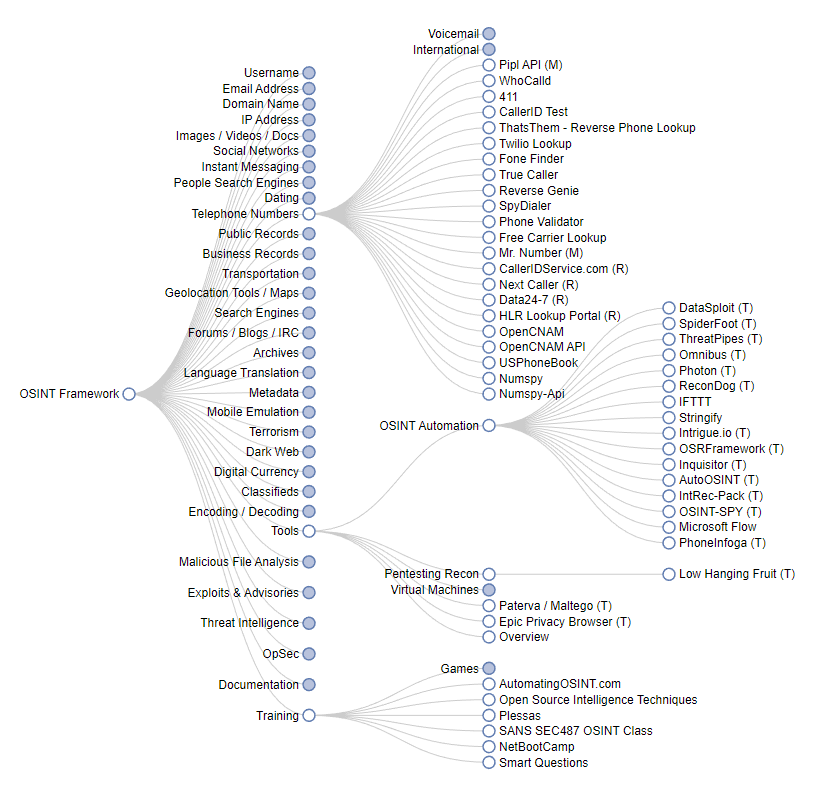
But, it can be pretty easy to skimp out on the “why”. This week I was learning about enumerating DNS. I knew the general flow of DNS, with the best visualization I could find below.
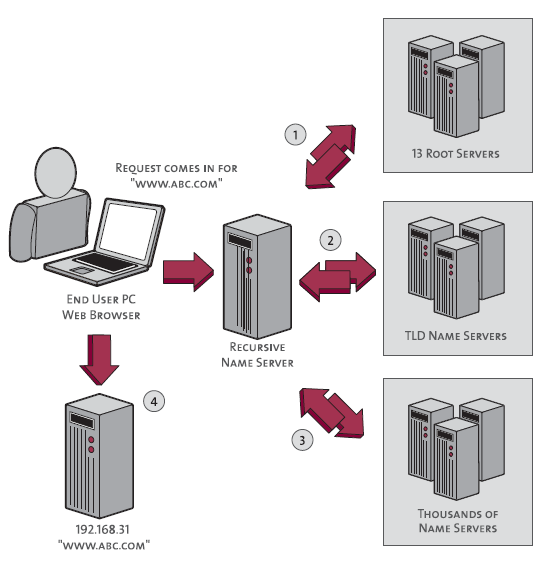
Misconfigured DNS servers can potentially expose private network maps to external parties through zone transfers. I learned about how to test a name server for zone transfers, but I wouldn’t say I’m equipped to explain the mechanics in detail.
I worry that I will be able to find and exploit weaknesses in systems, but not be able to communicate how that works to a wider audience. In my eyes, a good security tester can exploit a system and document it. A great one can explain why a system is vulnerable, communicate findings in the proper context to technical and nontechnical people, and work with administrators to fix it. My goal is to be the latter, even if the condensed timeframe and exam goals incentivize the former.
I’ll finish by saying the site I have found and bookmarked for use is the Open Source Intelligence (OSINT) Framework. The framework is a nice resource for finding tools to solve problems around information gathering. It was also a nice starting point for some of the passive intelligence gathering exercises.
Thank you all for reading! Also, if you’re a stranger on the internet who wants to tell me where I’m wrong, do it! I’ll even give you a shout out in the next post for whatever that is worth.
Finally, a quick update from my week 1 problem with a fake protocol: