Studying for the OSCP week 1
Journey Begins
In an attempt to further my professional career, I’m taking the Offensive Security Certified Professional (OSCP) exam in ~10 weeks. I’m in the security industry but I don’t have as much practical experience as I would like. On paper, I have a technical background, with undergraduate and graduate degrees in electrical engineering and computer science respectively. Those experiences have turned out to be, well, lacking in preparation for the workforce.
I’ll be summarizing my weeks in studying, pointing out things I found useful or any challenges I encountered. I know only 3 people will end up reading this, so I’ll keep it loose. Also, I do have a full-time job so that’s gonna take priority some weeks.
In my first full week I was able to commit to studying, I was able to get through most of the first 4 modules.
Everything I’ve gone through so far has mostly been review. I’ve had a good amount of practice on TryHackMe for learning tools and practicing on challenges. I take handwritten notes on most modules because I know I learn (and retain) information better when I write it out. I post the notes on the wall next do my desk and highlight all command syntax. They make for mediocre decoration but good cheat sheets ¯\_(ツ)_/¯. So to my partner’s chagrin, they’re staying up.
A review of reverse/bind shells was good. It was only the fourth time I’ve learned about them, so maybe this time something sticks.
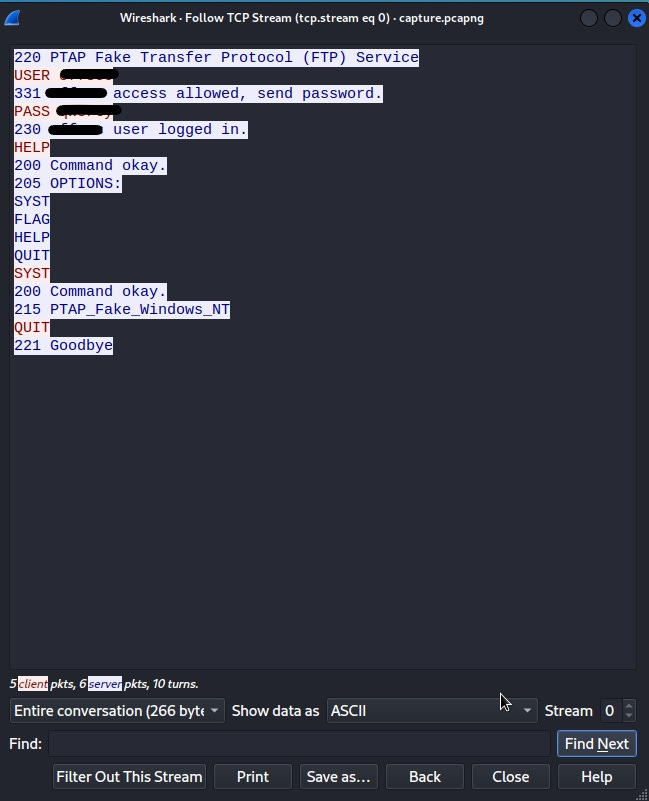
But there was one challenge in the “Practical Tools” topic that is absolutely driving me nuts. The section is about Wireshark, something I can always bumble my way around by googling everything. The challenge involves downloading a program and running it while using Wireshark. The program connects back to a server through a fake protocol that mimics FTP. I know it is fake because the challenge tells me that. It sends the username and password in cleartext. Once authenticated, there are some scripted packets sent running commands that give some information.
The entire session is only a couple hundred bytes. I was able to record it, follow the TCP stream and get it below. The question asked to grab the port, username and password. Done done and done. See below the followed TCP stream.
BUT here’s where things get tricky. We are told to log on to the server to retrieve the flag. I see in the TCP follow “FLAG” is one of the commands, so I know that must be important. So I try to log on to the server at with the previously learned port, and I am having a rough time.
Netcat and ssh aren’t connecting. I saw FTP earlier, let’s try it out. I’ll run an nmap scan on it too, just to be thorough. FTP was right! I could login.
┌──(kali㉿kali)-[~/offsec/Practicals_Tools]
└─$ ftp 192.168.137.52 -p 3084
Connected to 192.168.137.52.
220 PTAP Fake Transfer Protocol (FTP) Service
Name (192.168.137.52:kali): [USER]
331 [USER] access allowed, send password.
Password:
230 [USER] user logged in.
Great! Now time to run “FLAG” and submi- wait. What’s going on? Why is this FTP prompt punking me?
Remote system type is Command.
ftp> FLAG
?Invalid command.
ftp> flag
?Invalid command.
ftp> syst
225 Not a valid response. Please try again. Try HELP.
ftp> syst
200 Command okay.
ftp> system
215 PTAP_Fake_Windows_NT
ftp> syst
200 Command okay.
ftp> So to summarize, the flag command isn’t recognized. “SYST” which I got from the TCP follow image isn’t working either - or is it? That’s not a standard FTP command. I ran “help” and it looked like a normal FTP output. I tried so many of the commands: ls, cd, get, mget, etc. To be fair, I did not work my way through all of them, and this is the first time need to use the FTP terminal and not just bash one liners.
So my excited but increasingly more frustrated self starts to overengineer the hell out of a solution. I thought of the option to hand craft TCP packets to send. Let’s break that down.
Hand Crafting TCP packets:
Figure out if that’s a thing in Wireshark
Realize it isn’t
Google to see how someone smarter than you would do this
Arrive at inc0x0’s explanation
Kinda lose interest and question if you’re overthinking things
Honestly, it was a great explainer. If I need to, I’d probably do that. But doubt is festering in my mind, maybe I’m overthinking this?
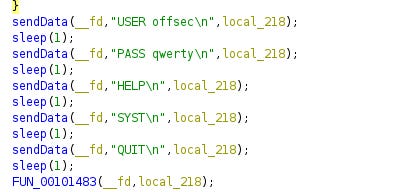
NO, I am not overthinking this enough. Let’s learn how to reverse engineer a program then dynamically insert the command I want - “FLAG” in for the “HELP” command. One download of Ghidra and an hour later, I actually make some progress in spite of having no idea what I’m doing.
I was able to find the point in the decompiled code where those commands are sent and renamed the function to “sendData”. I had done *something*.
I called that a W and went to bed after. I only dreamt about solving the problem once or twice.
~12 hours later I’m writing this post, still unsolved. I think I’m going to come back to it later with a fresh perspective. I’ve found two plausible ways that I’m confident will work, I just want another week. Maybe I’ll wake up on Tuesday in a fit and find the inspiration to keep going idk.
God if it isn’t peak Dunning Kruger to not solve the problem but feel so confident.
Congrats if you’ve somehow made it here. Follow me on twitter @louisfinney and subscribe to this Substack if you want watch someone fail over and over again.